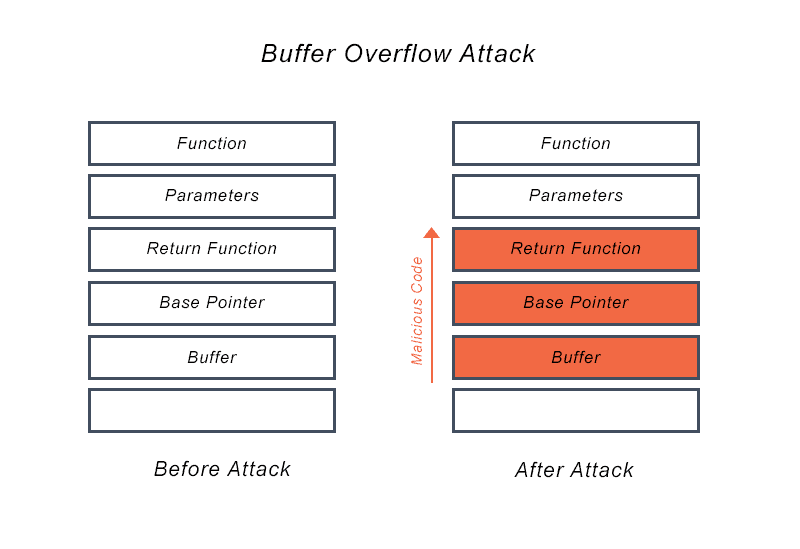
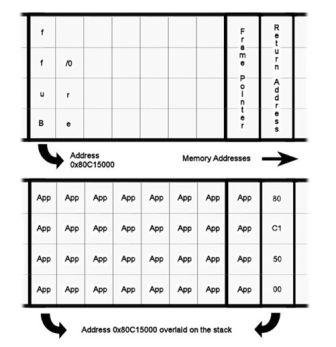
![PDF] The Buffer Overflow Attack and How to Solve Buffer Overflow in Recent Research | Semantic Scholar PDF] The Buffer Overflow Attack and How to Solve Buffer Overflow in Recent Research | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d59f80861f46722e4086b824e7de9c4ce52f5b35/4-Figure1-1.png)
PDF] The Buffer Overflow Attack and How to Solve Buffer Overflow in Recent Research | Semantic Scholar

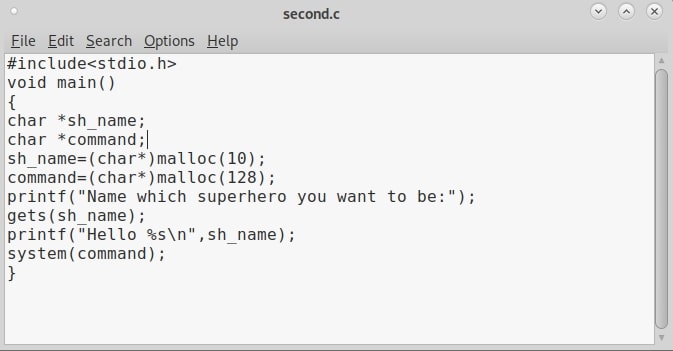
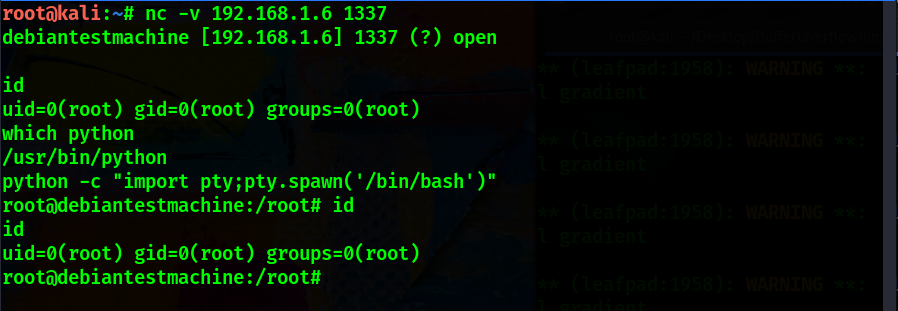
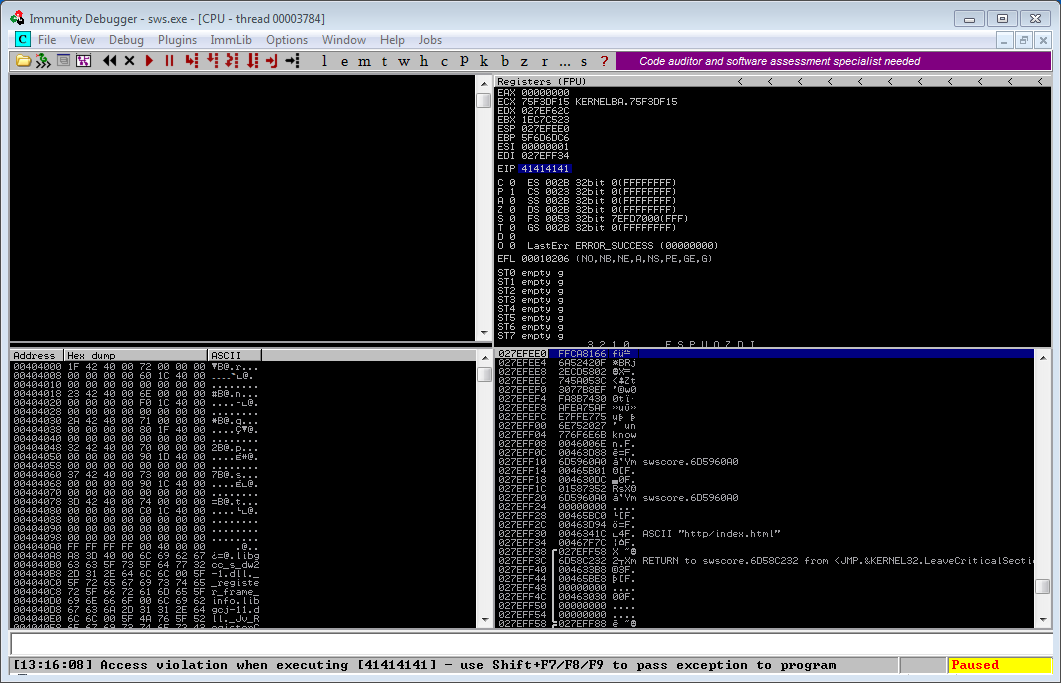
Hack Like a Pro: How to Build Your Own Exploits, Part 1 (Introduction to Buffer Overflows) « Null Byte :: WonderHowTo

Computer Forensics Use of Malicious Input. Buffer and Heap Overflow Attacks Standard Tool to Break Into Systems. Used for Access Escalation. Very Common. - ppt download